Computer Fundamental Concepts Quiz
Computer Fundamental (CACS 101)
Unit-1 Introduction to computer
A computer is an electronic machine that takes input from a user, processes the given input and generates output in the form of useful information.
A computer accepts inputs in many forms such as data, programs and user reply.
DATA -> raw details that require processing for generating useful information
PROGRAM -> set of instructions that can be executed by computer in sequential or non-sequential order
USER REPLY -> input provided by the user in response to query asked by computer
Characteristics
1. Speed
A computer can do any tasks in fractions of a second. The speed of the computer is based on its hardware configuration.
2. Storage Capacity
A computer can store a huge amount of data in many different formats.
3. Accuracy
A computer carries out any calculation with a 100% accuracy. However, this depends on the configuration of the system and instruction from the user.
4. Reliability
A computer process results with 0 error. Mostly the error generated in the computer is due to the user’s fault.
5. Diligence
A computer can be set to perform repetitive tasks for numerous times and the result will always be displayed with the same accuracy and efficiency. Computers aren’t affected by human traits like dizziness, fatigue, distraction, tiredness, etc.
6. Versatility
The same computer can be used for many different tasks for many different purposes.
Evolution of Computer
1. Mechanical Era
2. First Generation Computer
Employed: 1940 – 1956
Technology used: Vacuum Tube
Tasks done: Mathematical Calculation
Advantages: fast computing in their time, executed complex mathematical problems in an efficient manner
Disadvantages: Operated on machine language (0s and 1s), not flexible for running different applications, large and bulky in size and consumed high power
3. Second Generation Computer
Employed: 1956 – 1963
Technology Used: Transistors
Improvements: development of printer, secondary storage, operating system technology, replacement of machine language with assembly language
Tasks done: Mathematical Calculation
Advantages: fast computing in their time, easy to program (assembly language), smaller in size and consumed less power
Disadvantages: I/O devices not improved to a considerable extent, generated a huge amount of heat, beyond the access of households
4. Third Generation Computer
Employed: 1964 – 1975
Technology Used: Integrated Circuits (I.C.)
Improvements: I.C.s made the size of computer smaller, performance efficient and faster and reliable
Advantages: computational time reduced to nano-seconds, use of high-level language
Disadvantages: low storage, costly
5. Fourth Generation Computer
Employed: 1975 – 1989
Technology Used: LSI, VLSI
Improvements: GUI, new Operating System, development of LAN
Advantages: Size and cost minimized, accessible by home users
Disadvantages: complex microprocessor design and fabrication,
6. Fifth Generation Computer
Employed: 1989 onwards
Technology used: ULSI
Improvements: portable computers – laptop, pocket computer, PDA, etc. developed, developed parallel processing, invention of optical disk technology, Internet invented
Advantages: True AI, advanced parallel processing, portability, superconductor technology
Disadvantages: sophisticated and complex tools
Classification of Computer
| S.No. | Basis of Classification | Types |
|---|---|---|
| 1 | Operating Principle | Analog, Digital, Hybrid |
| 2 | Application | General Purpose, Special Purpose |
| 3 | Size and Capacity | Micro, Mini, Mainframe, Super Computer |
Anatomy of digital computer
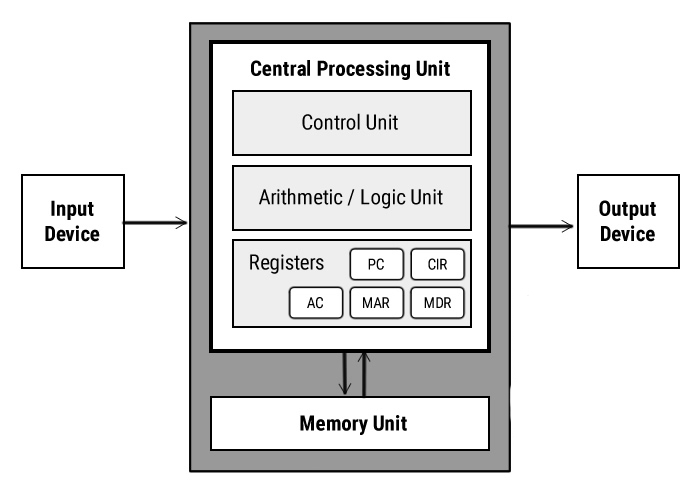
It is responsible for processing the data inside the computer system. It is also responsible for controlling all other components of the system.
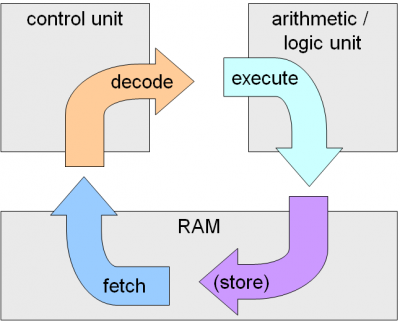
The main operation of the CPU includes four phases
– Fetching instruction from memory
– Decoding the instruction to decide what operation are to be performed
– Executing Instructions
– Storing the result back into memory
1. Arithmetic/ Logical Unit
ALU does arithmetic and logical operations. Arithmetic operations include addition, subtraction, multiplication and division. The arithmetic unit takes input instruction in the following form:
opcode + operand + format code
opcode – operation
operand – data
format code – format of the operand, e.g. fixed-point or floating-point
The logical unit operates the data logically. Logical operations include greater than (>), less than (<), equals to (=), not equal to (! =), shift left, shift right, etc. This unit makes use of logical gates (AND, OR, NAND, NOR, etc.) to perform logical operations.
2. Control Unit
This unit of CPU controls the flow of data and information. It maintains the sequence of operation being performed by the CPU. The control unit fetched instruction from storage area, decode the instructions and transmit the corresponding signal to ALU and the storage registers.
3. Main Memory
(discussed below)
2. Memory
1. Main Memory
RAM is the primary or main memory. It is volatile in nature and holds the data for a short period of time only, that is only until the system is running. Files and instructions are saved in different secondary storage systems and they are fetched to the RAM before the execution. This technique is known as swapping. Memory space available in the main memory directly affects the speed of the computer.
2. Cache Memory
It is the smallest and fastest form of memory. The contents that require to be fetched frequently are stored in the cache memory. Therefore, the processor before looking for the content in RAM checks here and goes to RAM only if the content isn’t available here.
Cache memory is always placed between RAM and the processor.
3. Register
There are special-purpose temporary storage units which are called registers. They are the form of memory with the highest transfer speed. These registers are used for holding instructions, data and intermediate results that are currently being processed.
Examples: Program Counter (PC), Instruction Register, Memory Address Register, Memory Buffer Register, Memory Data Register, Accumulator, etc.
3. Input Device
They are the computer peripherals that are used to send input signals to the computer for processing. The basic input device is keyboard.
Example: mouse, scanner, digital camera, etc.
4. Output Device
They are the computer peripherals that are used to display the results of the processed data. The basic output device is monitor.
Example: speaker, printer, etc.
5. Mass Storage Device
They are the peripherals that are used to store the processed data for future references.
Example: Hard Drive, Solid State Drive, flash drive, etc.
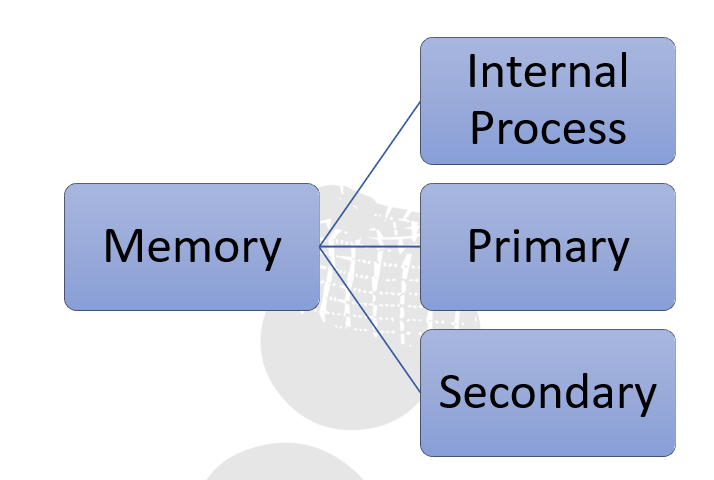
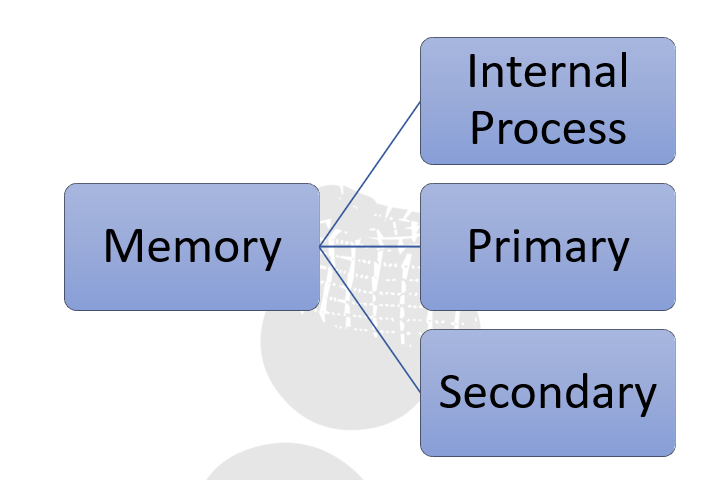
Memory and Storage System
Besides processing data and getting the results for immediate use computer is used for storing data as well. Therefore, there are two types of memory in a computer system, one for storing data that are currently being handled by the CPU and another for storing data and results for future reference.
The storage system used for handling the running process is called primary memory. They are temporary in nature. And the storage which is used to store data and information for longer-term is called secondary memory.
The data and information held by the primary memory can be directly accessed by the CPU using data and address buses. However, the data stored in the secondary memory is to be fetched to the primary memory through I/O channel first and the CPU reads the data from the secondary memory via the primary.
There is a third type of memory as well which is known as internal process memory. These are placed either near to the CPU or inside the CPU itself.
1 Byte = 8 Bits
1 KB = 1024 Bytes
1 MB = 1024 KB = 1048576 Bytes
1 GB = 1024 MB = 1073741824 Bytes
1 TB = 1024 GB = 1099511627776 Bytes
Primary Memory
It is volatile in nature and loses all its content once the power of the computer is turned off. Hence RAM is used for storing the data and instructions only during the processing. Unlike Secondary form of memory, it is faster in data transfer. It is the internal memory. It is also called Read/ Write memory as it can perform both read and write operations.
Ram can be further categorized into two types.
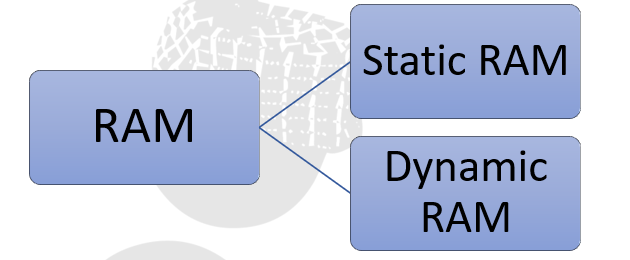
In this type of RAM data is stored only until the power of the computer is on. It uses numbers of transistors to store a single bit of data. Based on the functioning nature it can be further classified as
a. Asynchronous SRAM
It performs operations without the use of a system clock. It makes use of three signals for working, i.e. chip select (CS), write enable (WE) and output-enable (OE).
b. Burst SRAM
It works in association with the system clock. Therefore, it is also known as synchronous SRAM. It is used with high-speed applications as the read and writes cycles are synchronized with the clock cycle of the processor. The access waiting time gets reduced after the read and write cycle are synchronized.
c. Pipeline Burst SRAM
It uses the pipeline technology in which a large amount of data is broken up into different packets containing data. These packets are arranged in a sequential manner in a pipeline form and are sent to the processor simultaneously. It can handle a large amount of data at a very high speed. In fact, it is the fastest form of SRAM.
ii. Dynamic SRAM
In this type of RAM, data is stored in a storage cell consisting of transistors and capacitors. Unlike SRAM, DRAM needs to be refreshed continuously with the power supply because the capacitor has the tendency to get discharged. The DRAM is of four types.
i. Synchronous DRAM
It performs operations in association with the system clock cycle. It is used with the processor for storing data continuous manner. The continuous form of data storage helps in processing a greater number of instructions per unit time which ultimately increases the speed of data transfer.
ii. Rombus DRAM
It contains multiple addresses and data line that helps in increasing the data access speed. It is faster than Synchronous DRAM.
iii. Extended Data Out DRAM
It can access more than a bit of data at a time which helps in increasing data access rate. It allows to perform various tasks at a time such as read and write.
iv. Fast Page Mode DRAM
It makes use of paging in which read and write operation is performed by selecting the address of data from rows and columns of the matrix. Use of paging doesn’t allow the use of bus at the memory of 66 MHz because of which reading and writing data from matrix consumes a lot of time.
2. ROM
ROM stores data permanently. This means unlike RAM; it can retain data even after the computer is turned off. Generally, contents of ROM cannot be erased, modified or changed. Devices such as calculator, laser printer, etc. use ROM. It allows sequential access to data. It is divided into four types.
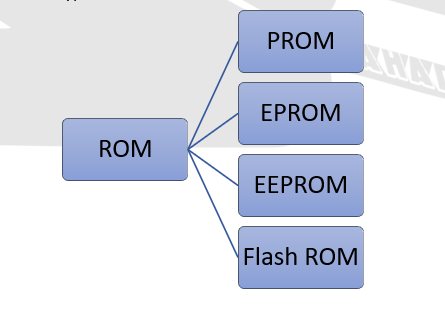
It is a memory chip on which write operation can be performed only once. The data on this ROM is written permanently and cannot be erased afterwards. The writing process on such ROM is called ‘Burning ROM’. It is mostly used in video games and electronic dictionaries.
ii. Erasable Programmable ROM (EPROM)
In such type of ROM, data can be erased or destroyed using Ultra-Violet (UV) rays. In such, the facility of changing the content is available. It facilitates the storage of data for longer terms.
iii. Electrically Erasable Programmable ROM (EEPROM)
It is the type of ROM in which data can be erased or destroyed electrically with the means of electric charge. Here, data can be written or read at the rate of one bit per unit time which makes it slow.
iv. Flash ROM (FROM)
It is a variation of EEPROM that uses floating gate transistors which can store data for a longer period of time. It is mainly used in mobile phones, digital cameras, etc. It is the fastest form of ROM. It uses continuous memory cells for storing data. It is of two types.
a. NAND Flash ROM
b. NOR Flash ROM
Secondary Memory/ Storage System
1. Magnetic Storage System
i. Magnetic Tapes
They are plastic tapes with a magnetic coating that are used for data storage. They are similar to normal recording tapes which can be used for storing audio and video. Data can be accessed sequentially.
Advantages:
– low cost and high storage
– easily transportable
– easy to handle and store
Disadvantages:
– low data transmission due to a sequential transmission
– low life duration
– required protected environment for storage
ii. Magnetic Disks
It is a flat disk covered with magnetic coating for holding information. It is used to store digital information in the form of small and magnetized needles. It is large in storage size and cheaper than RAM. It allows random access to data and provides the facility of erasing and recording data as many times as required.
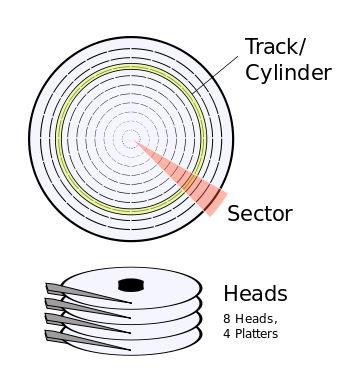
– High storage capacity and low cost
– Easy and direct access to data
– Less prone to corruption of data compared to magnetic tapes
Disadvantages:
– Prone to physical damage since it has a physical moving part
– Slower than SSDs
2. Optical Storage System
This storage system uses the laser light as the optical medium to retrieve as well as record data.
Example: CD-ROM, DVD, CR-R, CD-RW, DVD-R, DVD-RW
They are non-volatile and reliable compare to magnetic tapes.
Advantages:
– Large storage capacity
– Longer life-span than magnetic tapes
– Low ‘cost-per-bit’ for storage
– Portable
Disadvantages:
– Prone to scratches which could disturb or totally prevent the driver to perform R/W operations
3. Magneto-Optical System
It includes the features of both optical and magnetic disks. Its main objective is to store the data on personal computers for a longer period of time. It performs R/W operation by making use of laser and optical technology. It has ferromagnetic particles enclosed in a plastic coating. The laser beam used for R/W operation gets reflected due to magnetic surface of the disk.
It is slower in speed but its manufacturing cost is high.
4. Solid State Drive (SSD)
It is the device that contains all the properties of a hard drive to store the data and uses the solid-state memory which has no moving part. It uses semiconductors to store data. Its main principle is to process data electronically. Since it has no mechanical moving part, the data access time is faster than that in HDD.
Advantages:
– Better performance – high access speed, random access of data, faster R/W operation
– Low power consumption
– Highly reliable
– Small dimension/ compact size
Disadvantages:
– High cost
– Lower capacity
– Low storage density
– Vulnerable – data loss, affected by power loss, electrostatic discharges and magnetic fields
Interface
A system of interaction or communication between a computer and another entity such as printer, another computer network or a human user. Devices such as cable, network card, monitor or keyboard that enables interaction or communication between computer and other entity.
Interface is of three types.
1. Hardware Interface
Hardware interface exists in many of the components such as buses, storage devices, other I/O devices, etc. A hardware interface is described by mechanical, electrical and logical signal at the interface and protocols for sequencing them. Hardware interfaces can be parallel with several electrical connections carrying parts of data simultaneously or serially where data can be sent one bit at a time.
Serial -> 1 bit at a time
Parallel -> 1 word at a time
2. Software Interface
A software interface may refer to a wide range of different types of interface at different types of interfaces at different levels – an operating system may interface with a piece of hardware; application or program running on the operating system may need to interact via data streams, filters and pipelines. In Object oriented program, object within an application may need to interact via methods.
3. User Interface
A user interface consisting of a set of dials, knobs, operating system commands, graphical display formats and other devices provided by a computer or a program to allow the users to communicate or use the computer or program. The popular means of user interface is Graphical User Interface (GUI) which provides pictorial (picture-oriented) way to interact with the system. GUI is easier to use and user-friendly interface.
Mobile Computing
Mobile computing is human-interaction by which a computer is expected to be transported during normal usage which allows transmission of data and information in different available forms. This involves mobile communication, mobile hardware and mobile software.
• Mobile communication issues include ad-hoc networks and infrastructure networks as well as communication properties, protocols, data formats and concrete technologies.
• Mobile software deals with the characteristics and requirements of a mobile application.
Example: smartphone, smart card, laptop, wearable computer, etc.
Principles of Mobile Computing
1. Portability – facilitate movement of device within the mobile computing environment
2. Connectivity – availability to continuous connection w/ minimal lag & no interruption while movement
3. Social Interactivity – maintaining the connectivity to collaborate w/ other users
4. Individuality – adapting technology to meet individual needs
Unit-2 Computer Software
Contents: Introduction to Software, Types of Software, Program vs Software, Computer Virus and Antivirus
Among the two major components of a computer system, Software is one while Hardware being the other. Software refers to a set of computer programs and related data that provide the instructions for telling a computer what to do and how to do. It is a set of instructions that guides the hardware and tells it how to accomplish each task.
Hardware refers to the physical equipment that is necessary for performing various operations such as storing results and providing output to users in the desired form.
Types of Software
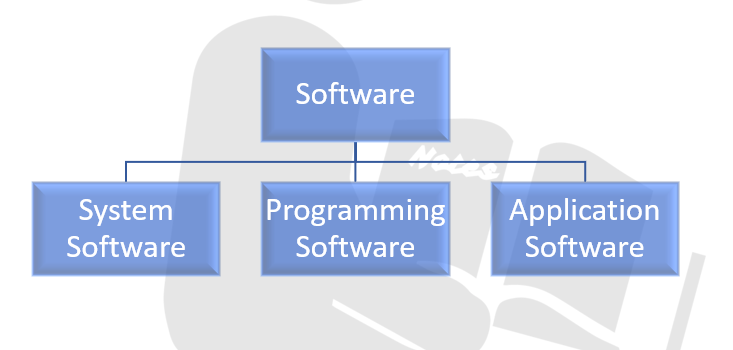
System Software
It is a type of computer software that is designed to operate the computer hardware so that the basic functionality and a platform for running application software are provided. Operating System and all other utility programs that manage computer resources at low level are system software.
Example: BIOS (Basic Input/ Output System) gets the computer system started after you turn it on, and it manages that data flow between the operating system and other attached devices such as hard disk, video adapter, etc. System utilities such as the disk defragmenter and system restore are also system software.
Programming Software
It includes tools in the form of programs or applications that software developers take in use to create, debug, maintain and support other programs and applications. Compiler, debugger, interpreter, linker and text editor are the parts programming software.
1. Compiler
They convert a high level language program into a low-level language program.
2. Assembler
They convert an assembly language program into low-level language programs.
3. Interpreter
It processes high-level language line by line and simultaneously produces low-level programs.
4. Linker
Most low-level languages allow the developer to develop a large program containing multiple modules. Linker arranges the object code of all the modules that have been generated by the language translator into a single program.
5. Debugger
It is a software that is used to detect the errors and bugs in programs. It locates the position of errors in the program codes.
6. Text editor
It is a program that allows the user to work with texts in a computer system. It is used for documentation purpose and enables us to edit information present in an existing document or file.
Example: C, C++, C#, BASIC, Java, Python, etc.
Application Software
It is a program of a group of programs designed for individual users. It allows end-users to accomplish one or more specific non-computer related task.
Example: Word processor, presentation software, data management system, desktop publisher, web browsers, etc.
Program vs Software
Software is the superset of programs in which one or many programs are executed sequentially or simultaneously to perform a particular job. It is the end product of a set of programs.
Example: MS-Excel
A program is a combination of lines of codes which takes input works on instruction on a computer to generate output. A program is the group of instructions which when performed will generate a logical output.
Example: addition or subtraction operation in MS-Excel
Summarizing, the program is a set of instructions that are executed by a computer, whereas software is a set of programs.
Example: the calculator is a software whereas addition, subtraction, etc. are set of programs that exist in the calculator
Computer Virus ad Antivirus
Computer Virus
A computer virus is a set of malicious code or program written to alter the way a computer operates. It is usually designed to spread from computer to computer. A virus operates by inserting or attaching itself to a legitimate program or document support macros in order to execute the codes.
A virus has the potential to cause unexpected or damaging effects such as harming system software by corrupting or damaging data. Once a virus successfully attaches itself to a program, file or document, the virus will remain dormant until circumstances cause a computer to execute its code. In order for a virus to infect any computer, the infected program has to be run in order for the code to be executed.
Signs of Computer Virus
1. Frequent pop-up windows
2. Changes your homepage
3. Mass email being sent from your email account
4. Frequent crashes
5. Slow computer performance
Different types of Virus
1. Boot sector virus
This type of virus can take control when you start or boot your computer. It spreads by plugging Flash drives.
2. Web scripting virus
This type of virus exploits the code of web browsers and webpages. It spreads through infected webpages.
3. Browser hijacker
This type of virus hijacks certain web browser functions and might automatically be directed to unintended sites.
4. Resident virus
This is the general type of virus that inserts itself in a computer system memory. A resident virus can execute at any time when the operating system loads.
5. Direct-action virus
This type of function comes into action when you execute a file containing a virus otherwise it remains dormant.
6. Polymorphic virus
A polymorphic virus changes its code each time the infected file is executed. It does this to invade antivirus.
7. File infector virus
This common virus inserts malicious code into executable files. i.e. files used to perform certain functions or operations on a system.
8. Macros virus
Macros virus are written in some macro language used for a software application. Such virus spread when you open an infected document often through an email attachment.
Antivirus
Antivirus is a type of program designed and developed to protect a computer from malware like computer virus, worm, spyware, botnets, boot-kits, keylogger, etc. Antivirus function to scan, detect and remove such viruses from the computer. Most antivirus incorporates both automated and manual filtering abilities. Instant scanning option may check files downloaded from the internet, disks that are embedded into PCs and files that are made by software installers.
Features of Antivirus
1. Default deny protection
It is implemented to prevent the entry of suspicious files by default.
2. Auto sand-box technology
A virtual environment where suspicious and unknown files are secluded and run to check for any malicious activity without interfering the normal operations.
3. Containment technology
It validates and authorizes the programs that are executable and ensure that processes are running without affecting the regular operation of the system.
4. Host intrusion protection system (HIPS)
It terminates any malicious activity once found. This prevents malware from infecting the operating system, registry keys, personal data or the system memory.
Unit-3 Operating System
Contents: Introduction, Functions and Types of Operating System and Open Source Operating System
An operating system is a software that makes the computer hardware to work while the computer hardware providers ‘raw computer power’, the operating system is responsible for making a computer more useful for users. The operating system provides an interface for users to communicate with the computer. It also manages the use of hardware, resources and enables proper implementation of application programs. In short, the operating system is the master of the control program of a computer.
The main function of the operating system includes:
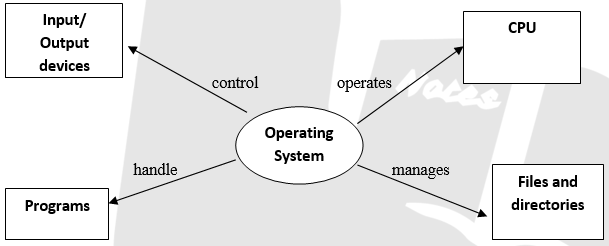
1. Operating CPU of the computer.
2. Controlling Input/ Output devices that provide an interface between the user and the computer.
3. Handling the working of application programs with the hardware and other software systems.
4. Managing the storage and retrieval of information using storage devices such as disks.
Functions of Operating System
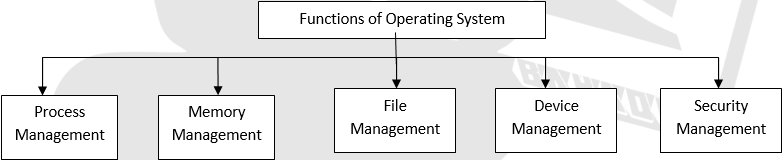
The main function of an operating system is t manage the resources such as memory and files of the computer system. The operating system also resolved the conflicts that arise when two users or programs request the same resources at the same time. Therefore it is also called resource manager of a computer. Some of the important functions of an operating system are:
1. Process management
It manages the processes running in the computer system process. A process is basically a program that is being currently run by a user or a computer.
Example: A word processor application program such as MS Word runs processes in a computer system.
2. Memory Management.
It manages the memory resources of a computer system. There are various resources of computer including primary memory or Random-Access Memory (RAM) and secondary memory like CDs and HDs. All the programs are loaded in the main memory before their execution. It is the function of the operating system to determine how much memory should we provide at each process.
3. File Management
It manages the files and directories of a computer system. A file can be defined as a collection of information or data that is stored in the memory of a computer system. Every file has a unique mane associated with it. The organization of files and directories in a computer system is referred to as a file system. An operating system allows users to create, modify, save or delete files in a computer system.
4. Device Management
The operating system deals with the management of peripheral devices such as printer, mouse and keyboard attached to a computer system. An operating system interacts with the hardware devices through a specific device driver. The primary task of the operating system is to manage the input/ output operation performed by end-users.
5. Security Management.
It ensures security for a computer system from various threats such as virus attack and unauthorized access. An operating system uses various technologies such as authentication, authorization, cryptography, etc. for ensuring the security of a computer system.
Types of Operating System
Based on the capabilities and the types of application supported, the operating system can be divided into six major categories viz.
1. Batch Processing Operating System
They are capable of executing only one job at a time. The jobs a program submitted by different users are grouped into batches and one batch of the job is to provide as input to the computer system at a time. The jobs in the batch are processed on a first come first serve basis. After execution of one job is completed the operating system automatically fetches the next job from the batch without any human intervention.
Advantages:
a) They were very efficient in their time as idle time for these computers is very less.
b) The OS facilitates execution of jobs in an organized manner.
Disadvantages:
a) Jobs are processed only in the order they are places and not per user’s priority.
b) Debugging of a program at execution is not possible.
c) The executing jobs may enter an infinite loop as each job is not associated with proper times.
2. Multi-user Operating System
The multi-user operating system enables multiple users to use the resource of a computer system at the same time. It allows a number of users to work simultaneously on the same computer. It is usually implemented by following multiterminal configuration. In the configuration, a single powerful computer is connected to multiple terminals through serial ports. The computer system is responsible for processing different requests generated by various terminals at a time. The control computer is equipped with a fast processor and a memory of large capacity for catering to multiple requests of end-users.
Example: Linux, Unix, VM-386, etc.
Advantages
a) Allows resources of a computer to be utilized an inefficient manner.
b) It enhances the overall productivity of various users by providing simultaneous access to various computer resources.
Disadvantages
a) It is complex and hence difficult to handle and maintain.
b) It may result in inconsistent data if activities of a user aren’t protected from other users.
c) It is required to have a robust security mechanism.
3. Multitasking Operating System
The multitasking operating system allows users to carry out multiple tasks at the same time on a single computer system. The multitasking OS are also known as several other names such as multi-processing, multi-programming, concurrent, or process scheduling operating system. In this type of operating system, different processes are executed simultaneously by implementing the concept of time slicing. According to this concept, a regular slice of CPU time is provided to each of the processes running in the computer system. It can be of two types, viz.
a) Preemptive Multitasking Operating System
In this OS, a slice of CPU time is allocated on some priority basis.
b) Co-operative Multitasking Operating System
In this OS, time slices of CPU are assigned to the process depending on whether or not to give up CPU control for other running processes.
Example: UNIX, Windows 2000, Linux, Windows XP.
Advantages:
a) It helps in increasing the overall performance of the system.
b) It helps in increasing the overall productivity of the user by performing a number of tasks at the same time.
Disadvantages:
a) A large amount of memory is required to execute several programs at a time.
b) Some mechanisms need to be implemented to ensure that the activity of one process does not interfere with the activities of other processes.
4. Rest- time Operating System
The real-time operating system is similar to the multi-tasking operating system in its functionality. However, these OS are specially designed and developed for handling real-time applications or embedded applications. The real-time applications are those critical applications that are required to be executed within a specific period of time.
Example of real-time applications is; industrial robots, space-crafts, industrial control applications.
It is of two types, viz.
a) Head Real-time OS
It is a type of OS where it is necessary to perform a task in a specified amount of time.
b) Soft Real-time OS
In Soft Real-time OS, a task can be performed even after its allocated time has elapsed.
Example: M tox, Lynx, RTX
Advantages:
a) It is easy to design, develop and execute the real-time application under the real-time OS.
b) It is usually more compact as compared to other operating systems hence requires less memory.
Disadvantages:
a) It is primarily focused on optimizing the execution time of an application and thus it sometimes overlooks some of the other critical factor related to the overall efficiency of the computer system.
b) It is used only for providing some dedicated functionality and cannot be used as a general-purpose OS.
5. Multiprocessor Operating System
Multiprocessor OS allows the use of multiple CPUs in a computer system for execution of multiple processes at the same time. The processes are executed faster compared to a single processor.
Example: Linux, UNIX, Windows 2000, etc.
Advantages
a) It helps in improving the overall efficiency and throughput of a computer system.
b) It helps in increasing the reliability of a computer. If one CPU fails, the other CPU takes control and execute the currently running processes.
Disadvantages:
a) Cost is very high.
b) A large amount of memory is required for running and executing several users program.
6. Embedded Operating System
It is somewhat similar to the real-time OS. The embedded OS is installed on an embedded computer system which is used for performing a computational task in electronic devices. This OS provides limited functionality that is required for the corresponding embedded computer system.
Example: Palm OS, Window CE.
Advantages:
a) It allows the implementation of an embedded system in an efficient manner.
b) A system with an embedded OS is easy to use and maintain.
Disadvantages:
a) It is possible to perform some specific operation with those OS.
b) This OS cannot be used in a frequently changing environment.
Open Source Operating System
Open Source is a methodology or approach towards the design and development of software with the intention of giving the user the access to the code. If we use open source software, not only we will be able to use it but also be able to see how it works, debug it, modify it and redistribute it. Open source software is licensed in a way that marked it legal to use as many copies as user wants. There’s a core difference between open source and free software, both represent the same core idea but the open resource allows the commercial utilization of code with the motive of profit.
Example: Red hat gains significant revenue from sales, distribution, maintenance and consulting service provided by Open Source Software.
Being an open source program, program code of an open source operating system are available. The user can modify these codes and develop a new application according to their requirement. Example: Linux
Linux
It is an open-source powerful UNIX based OS which runs on varieties of platforms including Intel, SPARCE and Power PC. It is a multi-user, multi-tasking, multi-programming operating system mainly popular for server OS. It is distributed through different distributors such as Red Hat, Mandrate, Open Suse, Ubuntu, Slackware, Sobayon, Debian, Mandriva, Fedora, Genten, Granular Linux.
Unit-4 Database Management System
Contents: Introduction to Database Management System,
DBMS Models, SQL, Database Design and Data Security, Data Warehouse, Data
Mining, Database Administrator
What is Database?
A database is a collection of related data and data is a
collection of facts and figures that can be processed to produce information.
Mostly data represents recordable facts. Data aids in producing information,
which is based on facts. For example, if we have data about marks obtained by
all students, we can then conclude about toppers and average marks.
A database management system stores data in such a way that it becomes easier
to retrieve, manipulate, and produce information.
Characteristics of DBMS
Real-world entity:
A modern DBMS is more realistic and uses real-world entities
to design its architecture. It uses the behavior and attributes too. For
example, a school database may use students as an entity and their age as an
attribute.
Relation-based tables:
DBMS allows entities and relations among them to form
tables. A user can understand the architecture of a database just by looking at
the table names.
Isolation of data and application: A database system is entirely different than
its data. A database is an active entity, whereas data is said to be passive,
on which the database works and organizes. DBMS also stores metadata, which is
data about data, to ease its own process.
Less redundancy:
DBMS follows the rules of normalization, which splits a
relation when any of its attributes is having redundancy in values.
Normalization is a mathematically rich and scientific process that reduces data
redundancy.
Consistency:
Consistency is a state where every relation in a database
remains consistent. There exist methods and techniques, which can detect
attempt of leaving database in inconsistent state. A DBMS can provide greater
consistency as compared to earlier forms of data storing applications like
file-processing systems.
Query Language:
DBMS is equipped with query language, which makes it more
efficient to retrieve and manipulate data. A user can apply as many and as
different filtering options as required to retrieve a set of data.
Traditionally it was not possible where file-processing system was used
ACID Properties:
DBMS follows the concepts of Atomicity, Consistency,
Isolation, and Durability (normally shortened as ACID). These concepts are
applied on transactions, which manipulate data in a database. ACID properties
help the database stay healthy in multi-transactional environments and in case
of failure.
Multiuser and Concurrent Access:
DBMS supports multi-user environment and allows them to
access and manipulate data in parallel. Though there are restrictions on
transactions when users attempt to handle the same data item, but users are
always unaware of them.
Multiple views:
DBMS offers multiple views for different users. A user who
is in the Sales department will have a different view of database than a person
working in the Production department. This feature enables the users to have a
concentrate view of the database according to their requirements.
Security:
Features like multiple views offer security to some extent
where users are unable to access data of other users and departments. DBMS
offers methods to impose constraints while entering data into the database and
retrieving the same at a later stage. DBMS offers many different levels of
security features, which enables multiple users to have different views with
different features.
Database Models
Data models define how the logical structure of a database
is modelled. Data Models are fundamental entities to introduce abstraction in a
DBMS. Data models define how data is connected to each other and how they are
processed and stored inside the system.
Two types
Entity-Relationship Model
 Figure:
ER Model
Figure:
ER Model
Entity-Relationship (ER) Model is based on the notion of
real-world entities and relationships among them. While formulating real-world
scenario into the database model, the ER Model creates entity set, relationship
set, general attributes, and constraints.
ER Model is best used for the conceptual design of a
database.
ER Model is based on:
• Entities and their attributes.
• An entity in an ER Model is a real-world entity having properties called
attributes. Every attribute is defined by its set of values called domain.
For example, in a school database, a student is considered as an entity.
Student has various attributes like name, age, class, etc.
Relationships among entities
The logical association among entities is called
relationship. Relationships are mapped with entities in various ways. Mapping
cardinalities define the number of associations between two entities.
Relational Model
 Figure:
Relational Model
Figure:
Relational Model
The most popular data model in DBMS is the Relational Model.
It is a more scientific model than others. This model is based on first-order
predicate logic and defines a table as an n-ary relation.
The main highlights of this model are:
1. Data is stored in tables called relations.
2. Relations can be normalized.
3. In normalized relations, values saved are atomic values.
4. Each row in a relation contains a unique value
5. Each column in a relation contains values from the same domain.
SQL (Structured Query Language)
What is SQL?
SQL is Structured Query Language, which is a computer language for storing,
manipulating and retrieving data stored in relational database. SQL is the
standard language for Relation Database System. All relational database
management systems like MySQL, MS Access, Oracle, Sybase, Informix, postgres
and SQL Server use SQL as standard database language.
Why SQL?
Allows users to access data in relational database management systems.
Allows users to describe the data.
Allows users to define the data in database and manipulate that data.
Allows embedding within other languages using SQL modules, libraries &
pre-compilers.
Allows users to create and drop databases and tables
SQL Process
When you are executing an SQL command for any RDBMS, the
system determines the best way to carry out your request and SQL engine figures
out how to interpret the task.
There are various components included in the process. These components are
Query Dispatcher, Optimization Engines, Classic Query Engine and SQL Query
Engine, etc. Classic query engine handles all non-SQL queries, but SQL query
engine won’t handle logical files
SQL Commands
The standard SQL commands to interact with relational databases are CREATE,
SELECT, INSERT, UPDATE, DELETE and DROP. These commands can be classified into
groups based on their nature.
DDL
Data Definition Language:
CREATE
Creates a new table, a view of a table, or another object in the database
ALTER
Modifies
an existing database object, such as a table.
DROP
Deletes
an entire table, a view of a table or other object in the database.
DML
Data Manipulation Language:
INSERT
Creates a record
UPDATE
Modifies records
DELETE
Deletes records
DCL
Data Control Language:
GRANT
Gives a privilege to the user
REVOKE
Takes back privileges granted from user
DQL
Data Query Language:
SELECT
Retrieves certain records from one or more tables
Unit-5 Data Communications and Computer Network
Contents: Introduction to
Communication system, Modes of Communication, Introduction to Computer
Network, LAN Topologies,
Transmission Media, Network Devices, OSI Reference Model, Communication
Protocols, Centralized vs
Distributed System
Introduction to Data Communication
Data communications are the
exchange of data between two devices via some form of transmission
medium such as a wire cable.
For data communications to occur,
the communicating devices must be part of a communication system
made up of a combination of
hardware (physical equipment) and software (programs).
Fundamental Characteristics
The effectiveness of a data
communications system depends on four fundamental characteristics:
delivery, accuracy, timeliness,
and jitter.
1. Delivery
The system must deliver data to
the correct destination. Data must be received by the intended
device or user and only by that
device or user.
2. Accuracy.
The system must deliver the data
accurately. Data that have been altered in transmission and
left uncorrected are unusable
3. Timeliness.
The system must deliver data in a
timely manner. Data delivered late are useless. In the case of
video and audio, timely delivery
means delivering data as they are produced, in the same order
that they are produced, and
without significant delay. This kind of delivery is called real-time
transmission.
4. Jitter
Jitter refers to the variation in
the packet arrival time. It is the uneven delay in the delivery of
audio or video packets
Components of Data Communication
A data communications system has
five components
Fig: Components of Data
Communication
1. Message
The message is the information
(data) to be communicated. Popular forms of information
include text, numbers, pictures,
audio, and video.
2. Sender
The sender is the device that
sends the data message. It can be a computer, workstation,
telephone handset, video camera,
and so on.
3. Receiver
The receiver is the device that
receives the message. It can be a computer, workstation,
telephone handset, television, and
so on.
4. Transmission medium
The transmission medium is the
physical path by which a message travels from sender to
receiver. Some examples of
transmission media include twisted-pair wire, coaxial cable, fiber-
optic cable, and radio waves.
5. Protocol
A protocol is a set of rules that
govern data communications. It represents an agreement
between the communicating devices.
Mode of Data Communication
Communication between two devices
can be simplex, half-duplex, or full-duplex
Simplex:
In simplex mode, the communication
is unidirectional, as on a one-way street. Only one of the two
devices on a link can transmit;
the other can only receive. Keyboards and traditional monitors are
examples of simplex devices. The
keyboard can only introduce input; the monitor can only accept
output. The simplex mode can use
the entire capacity of the channel to send data in one direction.
Half-Duplex:
In half-duplex mode, each station
can both transmit and receive, but not at the same time. When one
device is sending, the other can
only receive, and vice versa. In a half-duplex transmission, the entire
capacity of a channel is taken
over by whichever of the two devices is transmitting at the time. Walkie-
talkies and CB (citizens band)
radios are both half-duplex systems. The half-duplex mode is used in cases
where there is no need for
communication in both directions at the same time; the entire capacity of
the channel can be utilized for
each direction
Full-Duplex:
In full-duplex both stations can
transmit and receive simultaneously. The full-duplex mode is like a two
way street with traffic flowing in
both directions at the same time. In full-duplex mode, signals going in
one direction share the capacity
of the link: with signals going in the other direction. One common
example of full-duplex
communication is the telephone network. When two people are communicating
by a telephone line, both can talk
and listen at the same time. The full-duplex mode is used when
communication in both directions
is required all the time. The capacity of the channel, however, must
be divided between the two
directions.
Data Flow in different modes
Computer Network
A computer network is a group of
computer systems and other computing hardware devices that are
linked together through
communication channels to facilitate communication and resource-sharing
among a wide range of users.
Network Criteria
A network must be able to meet a
certain number of criteria. The most important of these are
performance, reliability, and
security
1. Performance:
Performance can be measured in
many ways, including transit time and response time. Transit
time is the amount of time
required for a message to travel from one device to another.
Response time is the elapsed time
between an inquiry and a response. The performance of a
network depends on a number of
factors, including the number of users, the type of
transmission medium, the
capabilities of the connected hardware, and the efficiency of the
software.
2. Reliability:
Network reliability is measured by
the frequency of failure, the time it takes a link to recover
from a failure, and the network's
robustness in a catastrophe.
3. Security:
Network security issues include
protecting data from unauthorized access, protecting data from
damage and development, and
implementing policies and procedures for recovery from
breaches and data losses.
Types of Connections
There are two types of
connections.
1. Point-to-Point
A point-to-point connection
provides a dedicated link between two devices. The entire capacity
of the link is reserved for
transmission between those two devices.
2. Multipoint
A multipoint (also called
multidrop) connection is one in which more than two specific devices
share a single link.
In a multipoint environment, the
capacity of the channel is shared, either spatially or temporally.
If several devices can use the
link simultaneously, it is a spatially shared connection. If users
must take turns, it is a
timeshared connection.
Types of Computer Network
Networks may be divided into
different types and categories according to four different criteria
1. Geographic spread of nodes and
hosts
When the physical distance between
the hosts is within a few kilometers, the network is said to
be a Local area Network (LAN).
LANs are typically used to connect a set of hosts within the same
building (e.g., an office
environment) or a set of closely-located buildings (e.g., a university
campus)
For larger distances, the network
is said to be a Metropolitan Area Network (MAN) or a Wide
Area Network (WAN). MANs cover
distances of up to a few hundred kilometers and are used for
interconnecting hosts spread
across a city.
WANs are used to connect hosts
spread across a country, a continent, or the globe
2. Access restrictions
Most networks are for the private
use of the organizations to which they belong; these are
called private networks. Networks
maintained by banks, insurance companies, airlines,
hospitals, and most other
businesses are of this nature
Public networks, on the other
hand, are generally accessible to the average user, but may
require registration and payment
of connection fees. Internet is the most-widely known
example of a public network.
3. Communication model employed by
the nodes
The communication between the
nodes is either based on a point-to-point model or a broadcast
model.
4. Switching model employed by the
nodes
In the point-to-point model, nodes
either employ circuit switching or packet switching. In circuit
switching, a dedicated
communication path is allocated between A and B, via a set of
intermediate nodes. In packet
switching, data is divided into packets (chunks of specific length
and characteristics) which are
sent from A to B via intermediate nodes. Each intermediate node
temporarily stores the packet and
waits for the receiving node to become available to receive it
LAN Topologies
Various topologies are possible for the broadcast LAN
such as bus, ring or mesh topology.
1. BUS Topology
A bus topology is multipoint. One long cable act as a
backbone to link all the devices in a
network. Nodes are connected to the bus cable by drop
lines and taps.
As a signal travels along the backbone, some of its
energy is transformed into heat. Therefore, it
becomes weaker and weaker as it travels farther and
farther. For this reason, there is a limit on
the number of taps a bus can support and on the distance
between those taps.
Fig: Bus Topology
2. Ring Topology
In a ring topology, each device has a dedicated
point-to-point connection with only the two
devices on either side of it. A signal is passed along
the ring in one direction, from device to
device, until it reaches its destination. Each device in
the ring incorporates a repeater. When a
device receives a signal intended for another device, its
repeater regenerates the bits and
passes them along.
Fig: Ring Topology
3. Star Topology:
In a star topology, each device has a dedicated
point-to-point link only to a central controller,
usually called a hub. The devices are not directly linked
to one another. Unlike a mesh topology,
a star topology does not allow direct traffic between
devices. The controller acts as an
exchange: If one device wants to send data to another, it
sends the data to the controller, which
then relays the data to the other connected device.
Fig: Star Topology
4. Mesh Topology
In a mesh topology, every device has a dedicated
point-to-point link to every other device. The
term dedicated means that the link carries traffic only
between the two devices it connects.
Fig: Mess Topology
Transmission Media
A transmission medium can be broadly defined as anything
that can carry information from a source to a
destination. The transmission medium is usually free
space, metallic cable, or fiber-optic cable. The
information is usually a signal that is the result of a
conversion of data from another form.
Guided Media
A signal traveling along any of these media is directed
and contained by the physical limits of the
medium. Twisted-pair and coaxial cable use metallic
(copper) conductors that accept and transport
signals in the form of electric current. Optical fiber is
a cable that accepts and transports signals in the
form of light.
1. Twisted-Pair Cable
A twisted pair consists of two conductors (normally
copper), each with its own plastic insulation,
twisted together. One of the wires is used to carry
signals to the receiver, and the other is used
only as a ground reference. The signal sent by the sender
on one of the wires causes
interference (noise) and crosstalk creating unwanted
signals. Twisting the pair of cable reduces
interference and cross talk between signals. For example,
Twisted-pair cables are used in
telephone lines to provide voice and data channels.
2. Coaxial Cable
Coaxial cable (or coax) carries signals of higher
frequency ranges than those in twisted pair
cable. Instead of having two wires, coax has a central
core conductor of solid or stranded wire
(usually copper) enclosed in an insulating sheath, which
is, in turn, encased in an outer
conductor of metal foil, braid, or a combination of the
two.
3. Fiber Optic Cable:
A fiber-optic cable is made of glass or plastic and
transmits signals in the form of light. To
understand optical fiber, we first need to explore
several aspects of the nature of light. Optical
fibers use reflection to guide light through a channel. A
glass or plastic core is surrounded by a
cladding of less dense glass or plastic. The difference
in density of the two materials must be
such that a beam of light moving through the core is
reflected off the cladding instead of being
refracted into it.
Advantages
• Higher bandwidth. Fiber-optic cable can support
dramatically higher bandwidths
• Less signal attenuation. Fiber-optic transmission
distance is significantly greater than
that of other guided media. A signal can run for 50 km
without requiring regeneration.
• Immunity to electromagnetic interference.
Electromagnetic noise cannot affect fiber-
optic cables.
• Resistance to corrosive materials. Glass is more
resistant to corrosive materials than
copper.
• Light weight. Fiber-optic cables are much lighter than
copper cables.
• Greater immunity to tapping. Fiber-optic cables are
more immune to tapping than
copper cables. Copper cables create antenna effects that
can easily be tapped.
Disadvantages
• Installation and maintenance is difficult
• Unidirectional light propagation. Propagation of light
is unidirectional. If we need
bidirectional communication, two fibers are needed.
UNGUIDED MEDIA: WIRELESS
Unguided media transport electromagnetic waves without
using a physical conductor. This type of
communication is often referred to as wireless
communication. Signals are normally broadcast through
free space and thus are available to anyone who has a
device capable of receiving them.
Unguided signals can travel from the source to
destination in several ways: ground propagation, sky
propagation, and line-of-sight propagation
Network device
1. Repeaters
A repeater is a device that operates only in the physical
layer. Signals that carry information
within a network can travel a fixed distance before
attenuation endangers the integrity of the
data. A repeater receives a signal and, before it becomes
too weak or corrupted, regenerates
the original bit pattern. A repeater does not actually
connect two LANs; it connects two
segments of the same LAN.
2. Bridges or Link Layer Switches
A bridge or Link layer switch (or simply Switch) operates
in both the physical and the data link
layer. As a physical layer device, it regenerates the
signal it receives. As a data link layer device,
the bridge can check the physical (MAC) addresses (source
and destination) contained in the
frame. A bridge has filtering capability. A bridge has a
table that maps addresses to ports.
3. Hubs
A Hub is a device that operates only in the physical
layer. It is basically used for connecting
stations in a physical star topology. The main
disadvantage of Hub is that it broadcast data to all
the devices connected to it. So, chances of collision and
data corruption is high in hubs.
4. Routers
A router is a three-layer device that routes packets
based on their logical addresses (host-to-
host addressing). A router normally connects LANs and
WANs in the Internet and has a routing
table that is used for making decisions about the route.
The routing tables are normally dynamic
and are updated using routing protocols.
There are three major differences between a router and a
repeater or switch.
• A router has a physical and logical address for each of
its interfaces.
• A router acts only on those packets in which the link
layer destination address matches
the address of the interface at which the packet arrives.
• A router changes the link layer address of the packet
when it forwards the packet
5. Gateway
A gateway is normally a computer that operates in all
five layers of the Internet or seven layers
of OSI model. A gateway takes an application message,
reads it, and interprets it. This means
that it can be used as a connecting device between two
internetworks that use different models
OSI Reference Model
The model is called the ISO-OSI (Open Systems
Interconnection) Reference Model because it deals with
connecting open systems—that is, systems that are open
for communication with other systems.
The OSI model is a layered framework for the design of
network systems that allows communication
between all types of computer systems. It consists of
seven separate but related layers, each of which
defines a part of the process of moving information
across a network.
The OSI model is composed of seven ordered layers:
physical (layer 1), data link (layer 2), network (layer
3), transport (layer 4), session (layer 5), presentation
(layer 6), and application (layer 7).
As the message travels from A to B, it may pass through
many intermediate nodes. These intermediate
nodes usually involve only the first three layers of the
OSI model
Fig: OSI-ISO Reference Model
Physical Layer
The physical layer coordinates the functions required to
carry a bit stream over a physical medium. It
deals with the mechanical and electrical specifications
of the interface and transmission medium. It also
defines the procedures and functions that physical
devices and interfaces have to perform for
transmission to occur.
Data Link Layer
The data link layer transforms the physical layer, a raw
transmission facility, to a reliable link. It makes
the physical layer appear error-free to the upper layer
(network layer).
Other responsibilities of the data link layer include the
following
• Framing - The data link layer divides the stream of
bits received from the network layer into
manageable data units called frames
• Physical addressing
• Flow control - If the rate at which the data are
absorbed by the receiver is less than the rate at
which data are produced in the sender, the data link
layer imposes a flow control mechanism to
avoid overwhelming the receiver
• Error control - The data link layer adds reliability to
the physical layer by adding mechanisms to
detect and retransmit damaged or lost frames. It also
uses a mechanism to recognize duplicate
frames. Error control is normally achieved through a
trailer added to the end of the frame
• Access control - When two or more devices are connected
to the same link, data link layer
protocols are necessary to determine which device has
control over the link at any given time
Network Layer
The network layer is responsible for the
source-to-destination delivery of a packet, possibly across
multiple networks (links). Whereas the data link layer
oversees the delivery of the packet between two
systems on the same network (links), the network layer
ensures that each packet gets from its point of
origin to its final destination.
Other responsibilities of the network layer include the
following:
• Logical addressing - The physical addressing
implemented by the data link layer handles the
addressing problem locally. If a packet passes the
network boundary, we need another
addressing system to help distinguish the source and
destination systems. The network layer
adds a header to the packet coming from the upper layer
that, among other things, includes the
logical addresses of the sender and receiver.
• Routing - When independent networks or links are
connected to create internetworks (network
of networks) or a large network, the connecting devices
(called routers or switches) route or
switch the packets to their final destination. One of the
functions of the network layer is to
provide this mechanism.
Transport Layer
The transport layer is responsible for process-to-process
delivery of the entire message. A process is an
application program running on a host. Whereas the
network layer oversees source-to-destination
delivery of individual packets, it does not recognize any
relationship between those packets. It treats
each one independently, as though each piece belonged to
a separate message, whether or not it does.
The transport layer, on the other hand, ensures that the
whole message arrives intact and in order,
overseeing both error control and flow control at the
source-to-destination level.
Other function includes
• Connection control - The transport layer can be
either connectionless or connection oriented.
• Flow control - Like the data link layer, the transport
layer is responsible for flow control.
However, flow control at this layer is performed end to
end rather than across a single link.
• Error control Like the data link layer, the transport
layer is responsible for error control.
However, error control at this layer is performed
process-to-process rather than across a single
link. The sending transport layer makes sure that the
entire message arrives at the receiving
transport layer without error (damage, loss, or
duplication). Error correction is usually achieved
through retransmission.
Session Layer
The services provided by the first three layers
(physical, data link, and network) are not sufficient for
some processes. The session layer is the network dialog
controller. It establishes, maintains, and
synchronizes the interaction among communicating systems.
Specific responsibilities of the session layer include
the following:
• Dialog control - The session layer allows two systems
to enter into a dialog. It allows the
communication between two processes to take place in
either half duplex (one way at a time) or
full-duplex (two ways at a time) mode.
• Synchronization - The session layer allows a process to
add checkpoints, or synchronization
points, to a stream of data
Presentation Layer
The presentation layer is concerned with the syntax and
semantics of the information exchanged
between two systems
• Translation - Different computers use different
encoding systems, the presentation layer is
responsible for interoperability between these different
encoding methods. The presentation
layer at the sender changes the information from its
sender-dependent format into a common
format. The presentation layer at the receiving machine
changes the common format into its
receiver-dependent format
• Encryption - To carry sensitive information, a system
must be able to ensure privacy. Encryption
means that the sender transforms the original information
to another form and sends the
resulting message out over the network. Decryption
reverses the original process to transform
the message back to its original form.
• Compression - Data compression reduces the number of
bits contained in the information. Data
compression becomes particularly important in the
transmission of multimedia such as text,
audio, and video.
Application Layer
The application layer enables the user, whether human or
software, to access the network. It provides
user interfaces and support for services such as
electronic mail, remote file access and transfer, shared
database management, and other types of distributed
information services.
Specific services provided by the application layer
include the following:
• Network virtual terminal - A network virtual terminal
is a software version of a physical
terminal, and it allows a user to log on to a remote
host.
• File transfer, access, and management - This
application allows a user to access files in a remote
host (to make changes or read data), to retrieve files
from a remote computer for use in the
local computer, and to manage or control files in a
remote computer locally.
• Mail services - This application provides the basis for
e-mail forwarding and storage.
• Directory services - This application provides
distributed database sources and access for global
information about various objects and services.
Fig: OSI Layers as Software tasks
Communication Protocols
All communications between devices require that the
devices agree on the format of the data. The set
of rules defining a format is called a protocol. At the
very least, a communications protocol must define
the following:
• rate of transmission (in baud or bps)
• whether transmission is to be synchronous or
asynchronous
• whether data is to be transmitted in half-duplex or
full-duplex mode
In addition, protocols can include sophisticated
techniques for detecting and recovering from
transmission errors and for encoding and decoding data.
Centralized vs Decentralized
System
Distributed System
A distributed system is a collection of independent
computers that appear to the users of the system as
a single system. A Distributed system consists of
multiple autonomous computers, each having its own
private memory, communicating through a computer network.
Information exchange in a distributed
system is accomplished through message passing.
Examples
• World Wide Web (WWW) is the biggest example of
distributed system.
• The internet
• An intranet which is a portion of the internet managed
by an organization
• Network of branch office computers
Advantages of Distributed Systems over Centralized
Systems
• Economics - A collection of microprocessors offers a
better price/performance than
mainframes. Low price/performance ratio: cost effective
way to increase computing power.
• Speed - A distributed system may have more total
computing power than a mainframe. Ex.
10,000 CPU chips, each running at 50 MIPS. Not possible
to build 500,000 MIPS single processor
since it would require 0.002 sec instruction cycle.
Enhanced performance through load
distributing.
• Inherent distribution - Some applications are
inherently distributed. Ex. a supermarket chain.
• Reliability - If one machine crashes, the system as a
whole can still survive. Higher availability
and improved reliability.
• Incremental growth - Computing power can be added in
small increments. Modular expand-
ability
• Another deriving force - The existence of large number
of personal computers, the need for
people to collaborate and share information.
• Open system - This is the most important point and the
most characteristic point of a
distributed system. Since it is an open system it is
always ready to communicate with other
systems. An open system that scales has an advantage over
a perfectly closed and self-
contained system.
Unit -6 Internet and WWW
Contents:
-
Internet
- Introduction to Internet and its Applications
- Connecting to the Internet
- Client/Server Technology
- Internet as a Client/Server Technology
- Video-Conferencing
- Internet Service Providers
- Domain Name Server
- Internet Address
- Internet Protocols (IP, TCP, HTTP, FTP, SMTP, POP, Telnet, Gopher, WAIS)
- Introduction to Intranet, Internet vs. Intranet vs. Extranet
- Advantages & Disadvantages of Intranet
-
World Wide Web (WWW)
- World Wide Web and Its Evolution
- Architecture of Web
- Uniform Resource Locator (URL)
- Browsers
- Search Engine
- Web Servers: Apache, IIS, Proxy Server
- HTTP Protocol, FTP Protocol
Introduction to Internet
The Internet is a global system of interconnected computer networks that use the standard Internet protocol suite (TCP/IP) to serve billions of users worldwide. It is a network of networks that consists of millions of private, public, academic, business, and government networks, of local to global scope that are linked by a broad array of electronic, wireless, and optical networking technologies.
The Internet carries a vast range of information resources and services, such as the interlinked hypertext documents of the World Wide Web (WWW) and the infrastructure to support electronic mail.
Application of Internet
- E-mail - Email is now an essential communication tool in business. With email, you can send and receive instant electronic messages.
- 24/7 Availability - Internet is available 24 hours a day, 7 days a week, for usage.
- Information - Information is probably the biggest advantage the Internet offers. There is a huge amount of information available on the Internet for just about every subject, ranging from government law and services, trade fairs and conferences, market information, new ideas, and technical support.
- Services - Net banking, job searching, purchasing tickets, hotel reservations, guidance services, etc.
- E-commerce, Entertainment, Software downloads, etc.
Limitations of Internet
- Theft of Personal Information - Risk of personal data being stolen.
- Negative Effects on Family Communication - Overuse of the Internet affects interpersonal relationships.
- Internet Addiction - Excessive use can lead to addiction.
- Children Using the Internet - Exposure to inappropriate content.
- Virus Threats and Spamming - Risks include malicious software and unsolicited emails.
Connecting to the Internet
Many home and small business users connect to the Internet via high-speed broadband Internet service. With broadband Internet service, your computer or mobile device is usually connected to the Internet the entire time it is powered on. Examples of broadband Internet services include cable, DSL, fiber, radio signals, and satellite.
- Cable Internet Service - Provides high-speed Internet access through the cable television network via a cable modem.
- DSL (Digital Subscriber Line) - Provides high-speed Internet connections using regular copper telephone lines.
- Fiber to the Premises (FTTP) - Uses fiber-optic cable to provide high-speed Internet access to home and business users.
- Fixed Wireless - Provides high-speed Internet connections using a dish-shaped antenna on your house or business to communicate with a tower location via radio signals.
- Cellular Radio Network - Offers high-speed Internet connections to devices with built-in compatibility.
- Wi-Fi (Wireless Fidelity) Network - Uses radio signals to provide high-speed Internet connections to compatible or properly equipped wireless computers and devices.
- Satellite Internet Service - Provides high-speed Internet connections via satellite to a satellite dish that communicates with a satellite modem.
Syllabus
Course Title: Computer Fundamentals and Applications (4 Cr.)
Course Code: CACS101
Year/Semester: I/I
Class Load: 8 Hrs. / Week (Theory: 4 Hrs., Practical: 4 Hrs.)
This course offers fundamental concepts of computer and computing which includes introduction to computer system, computer software & database management system, operating system, data communication & computer network and contemporary technologies.
It also aims at helping students convert theoretical concept into practical skill through the use of different application packages including word processor, spreadsheet package, presentation package and photo editing graphical package.
Course Objectives
The general objectives of this course are to provide fundamental concepts of information and communication technology and to make students capable of using different application packages in their personal as well as professional life.
Course Contents
Unit 1 Introduction to Computer System [16 Hrs.]
Introduction to Computer, Characteristics of Computer, Applications of Computer, Classification of Computer, Mobile Computing, Anatomy of a Digital Computer, Computer Architecture, Memory & Its Classification, Input devices, Output Devices, Interfaces.
Unit 2 Computer Software [3 Hrs.]
Introduction to Software, Types of Software, Program vs. Software, Computer Virus and Antivirus.
Unit 3 Operating System [4 Hrs.]
Introduction to Operating System, Function of Operating System, Types of Operating System, Open-Source Operating System.
Unit 4 Database Management System [4 Hrs.]
Introduction to DBMS. Database Models, SQL, Database Design and Data Security, Data Warehouse, Data Mining, Database Administrator
Unit 5 Data Communication and Computer Network [10 Hrs.]
Introduction to communication system, Mode of Communication, Introduction to Computer Network, T3:’pes of Computer Network, LAN Topologies, Transmission Media, Network Devices, OSI Reference Model, Communication Protocols, Centralized vs. Distributed System.
Unit 6 Internet and WWW [6 Hrs.]
Internet: Introduction to Internet and its Applications, Connecting to the Internet, Client/Server Technology, Internet as a Client/Server Technology, Email, Video-Conferencing, Internet Service Providers, Domain Name Server, Internet Address, Internet Protocols (IP. TCP, HTTP, FTP, SMTP, POP, Telnet, Gopher, WAIS), Introduction to Intranet, Internet vs. Intranet vs. Extranet, Advantages & Disadvantages of Intranet
World Wide Web (WWW): World Wide Web and Its Evolution, Architecture of Web. Uniform Resource Locator (URL), Browsers: Internet Explorer, Netscape Navigator, Opera, Firefox, Chrome, Mozilla; Search Engine, Web Servers: Apache, Proxy Server; HTTP Protocol, FTP protocol.
Unit 7 Contemporary Technologies [13 Hrs.]
Multimedia, e-Commerce, e-Learning, e-Governance, e-Banking, Hypermedia, Geographical Information System, Virtual Reality, Augmented Reality, Artificial Intelligence, Ambient Intelligence, Robotics, Bit Coin.
Laboratory Works
Laboratory works should cover all the units and topics mentioned below and a project work should be carried out by students individually implementing the concept and skill learnt in this course.
Unit 1 Operating System [10 Hrs.]
GUI Based OS (5 Hrs.): Interface, GUI vs. CUI, Introduction to Windows, Features, Elements of Windows, Task Bar, Using Menus and Submenus, Opening a Program, Opening Multiple Program, Using Short Cuts, Using My Computer, Switching off the System, Desktop and Custom Wall Papers, Screen Saver, Using Help for Interactive Learning.
Using General Accessories: Notepad, Paint Tool, Clip Board, Character Map, Calculator etc.; Using Multimedia: Using CD/DVD/BD, Using Audio/Video; Using Explorer to Manage Files and Folders: Copy/Delete/Rename/Short Cuts; Recycle Bin and It Uses. Using Format, Scandisk and Disk Defragmenter, Windows Installation and Setting.
CUI Based OS (5 Hrs.): Introduction to DOS, DOS Internal Commands, DOS External Commands.
Unit 2 Word Processor [12 Hrs.]
Introduction to Word Processor, Features of Word Processor, Elements of Word Window, Creating & Saving Document, Copy Paste and Cut Paste, Format Painter, Undo and Redo, Print Preview, Printing Documents, Fonts, Effect and Character Formatting, Paragraph Formatting, Styles, Finding, Replacing and Selection, Cover Page, Blank Page, Page Break, Working with Table, Inserting Picture, Clip Art, Shapes,
Smart Art and ‘hart, Hyperlink, Bookmarks. Cross- Referencing, Header, Footer, Page Number, Working with Text Box, Quick Parts, Word Art, Drop Cap, Signature Line, Date & Time, Object. Equation, Symbol, Working with Themes, Page Margins, Page Orientation, Page Size, Columns Handling, Hyphenation, Watermark, Page Color, Page Borders, Indentation, Arranging Objects, Table of Contents, Footnote and Endnote,
Citation and Bibliography, Captions, Inserting Index, Table of Authorities, Mail Merge, Spelling and Grammar, Thesaurus, Translation, Word Count, Comments, Tracking, Changes, Compare, Protecting Document, Document Views, Ruler, Gridlines, Document Map, Thumbnails, Zooming, Window Handling, Creating and Using Macro.
Unit 3 Spreadsheet Package [12 Hrs.]
Introduction to Spreadsheet Package, Features of Spreadsheet Package, Introduction to Microsoft Excel, Elements of Excel Window, Cell Referencing in Excel: Relative, Absolute, and Mixed; Managing Workbooks, Worksheets, Windows, Working with Worksheet, Printing Worksheet, Using Formulas/functions; Formatting/Conditional Formatting Data & worksheet; Using Paste Special, Essential Worksheet Functions,
Using Templates, Protecting the File and Worksheet with Passwords; Working with Graphic Objects: Clip Art, Word Art, Map; Working with Charts, Working with Internal Database, Getting More Power from Worksheet Databases, Accessing External Databases, Loan Amortization Scheduling and Calculation; Data Validation, Consolidating and Outlining, Using What- if Analysis: Data Table, Goal Seek, Scenario Manager; Understanding Pivot Tables, Constructing and Analyzing Pivot Tables, Using Custom Controls on Worksheets, Effectively Using the Macro Recorder
Unit 4 Presentation Package [6 Hrs.]
Introduction, Creating and Saving Presentation; Entering, Editing, and Enhancing Text; Editing in different views- Outline View, Slide Sorter View; Creating Graphs, Editing and Enhancing Graphs; Adding ClipArt in Slide, Editing Arts, Animating Charts and Art Objects, Adding Sound, Choosing Sound Effects-Transitional, From Other Sources; Adding Sounds to Animations and Sound Objects; Recording Sound and Narration;
Adding Movie in Slides, Playing and Editing Movie; Making Movie Poster and Icon; Slide Show, Setting Slide Transition, Speed and Slide Advancement; Rehearsing Slide Display Timing, Slide Notes and Comments; Editing Text Color, Creating Custom Color; Background and Schemes; Linking and Embedding Objects; Importing and Exporting Presentation; Printing Slides and Handouts
Unit 5 Photo Editing Package 20 Hrs.
Fundamentals
Graphics Basics: Bitmap Vs. Vector-Based Graphics, Color/Bit Depth and linage Resolution, Graphic File Formats, Optimizing Web Graphics, Regular Text. Vs. Anti- Aliased Text, Pixel Resize Vs. Smart Resize, Regular Graphics Vs. Interlaced Graphics, Lossy Compression Vs. Lossless Compression, Dithered Graphics Vs. Non-Dithered Graphics, Standard Selection Vs. Floating Selection, Tolerance, Opacity.
Introduction to Color: Color Modes- RGB, CMYK, Grayscale, LAB, Bitmap; Hue, Saturation, and Brightness; Browser Safe Colors; Shadows, Highlights and Midtones of an Image.
Interface, Tools and Options:
Environment: About Photoshop, The Photoshop Interface, setting up a new Photoshop document, saving a new document, The Default Palettes, working with Photoshop Palettes, The Photoshop Toolbox and Options bar, Using Guides and Ruler,
Image and Color Basics: Supported import and export image formats, Opening an Image in Photoshop, Creating Images in Photoshop, Saving Images in Photoshop, Basic Image Editing, Changing Image Size, Cropping an Image, Changing Color/Bit Depth, Optimizing Images using Save for Web, Working with Color in Photoshop
Tools: Parts of the Toolbox, Toolbox Shortcuts, Tools Options, Marquees, Magic wand, Lassos, move tool, Crop tool, Slice tools, Pencil, Paintbrush, Eraser tools, History brushes, Clone Tamp-Pattern stamp, Healing brush tool, Retouch tool, Gradient, Paint bucket. Burn-Dodge-Sponge, Blur-SharpenSmudge. Shapes-line- rectangle-polygon-custom shapes, Path selection tool, Pen tool, Type tools, Notes Tool-Audio annotation, Eyedropper-Color Sampler-Measure tool, Hand-Zoom, Quick Mask-Screen modes, Jump to Image Ready, Back ground and Foreground.
Transforms: Using Free transform, Move, Rotate, Scale, Skew, Distort, Perspective, Flip-vertical, horizontal, Invert, rotate 180°, Rotate 90° CW, Rotate 90° CCW.
Layers, Channels and Actions
Photoshop Layers: About Layers-Fill and Adjustment Layers, The Layer Palette, Naming Layers, Creating Layers, Deleting Layers, Viewing Layers, Moving Layers, Layer Opacity, Locking Layers, Merging Layers, Layer Modes and Blending Options, Image Composting Using Layers.
Photoshop Channels: About Channels, The Channel Palette, Creating and Viewing Channels, Modifying Channels, Deleting Channels, Alpha Channels and Masks
Actions: Using the Action. Palettes; Recording Action, Playing Action, Editing Action, Loading a Saved Action.
Restoring and Enhancing Images
Restoration of Photos: Restoring Damaged Photos, Photo Retouching.
Photo Enhancement and Color Correction: Changing Levels, Changing Curves, Color Balance, Changing Brightness and Contrast, Changing Hue Saturation and Brightness, changing a Grayscale Image to a Colored Image, Histogram, Gradient Map, Desaturate, Invert, Color Replace, Selective Color, Equalize, Threshold, Channel Mixer, Posterize, Changing Background using Layer Composting
Text Editing and Special Effects
Text Editing in Photoshop: About the Type Layer, Creating Vertical and Horizontal Types, Point and Paragraph Text Creation, Using Horizontal and Vertical Type Mask Tools, Using Character Palette for Text Editing, Choosing a Font, Changing the Type Color, Choosing a Type Size, Specifying Kerning and Tracking, Using Fractional Character Widths, Specifying Baseline Shift, Applying Underline and Strikethrough, Text Alignment and Justification, Specifying Anti-Aliasing, Creating Text Warp, Rasterizing Type, Converting Ty–pe to Shapes, Adding Effects to Text
Photoshop Special Effects and Filters: About Special Effects, Using Filters, Basic Filter Examples, Artistic Filters, Distorting Filters, Filter Combinations, Plug-in Filters.
Web Application and Animation
Adobe Image Ready: About Image Ready, Opening Image Ready, The Image Ready Interface, Image Maps, Image Slicing, Basic Animation.
Photoshop for Building Web Interface: About the Interface
Teaching Methods
The teaching faculties are expected to create environment where students can update and upgrade themselves with the current scenario of computing and information technology with the help of topics listed in the syllabus. The general teaching pedagogy that can he followed by teaching faculties for this course includes class lectures, group discussions, case studies, guest lectures, research work, project work, assignments (theoretical and practical), and written and verbal examinations.
Evaluation
Text Books
1. Alexis Leon, Mathews Leon, “Fundamentals of Information Technology,2/e”, Vikas Publishing I louse Pvt Limited, 2009, ISBN: 9788182092457
2. E Balagurusamy, “Fundamentals of Computers,” Tata McGraw Hill Education PVT.Ltd., 2009, ISBN: 9780070141605
3. Peter Norton’s, “Introduction to Computers”, 7th Edition, Tata McGraw-Hill, 2010, ISBN: 9780070671201
Reference Books
1. Brad Davlev & DaNae Davley, “Adobe Photoshop CS6 Bible”, Wiley Publishing Inc., 2012, ISBN: 978-1-118-12388-1
2. Faiths Wempen, “Microsoft Office Power Point 2007 Bible (With CD)”, Wiley Publishing Inc., 2007, ISBN: 978-0470043684
3. Herb Tyson, “Microsoft Office Word 2007 Bible (With CD)”, Wiley Publishing Inc., 2007
4. Jim Boyce, “Windows 7 Bible “, Wiley Publishing Inc., 2009, ISBN: 978- 0470509098
5. John Walkenbach, “Microsoft Office Excel 2007 Bible (With CD)”, Wiley Publishing Inc., 2007, ISBN: 978-0470044032
6. Pradeep Sinha and Priti Sinha, “Computer Fundamentals (with C.D)”, 6th Edition, BPB Publications, 2003, ISBN: 9788176567527
7. Ramesh Rimal & et. al., “Computer Science-4 Revised Edition”, Buddha Academic Publishers and Distributors Pvt. Ltd. Nepal, 2013
8. Ramesh Rimal & et. al., “Computer Science-H, Revised Edition”, Buddha Academic Publishers and Distributors Pvt. Ltd. Nepal, 2013


No comments:
Post a Comment